Comprehensive Guide to VLANs: Design, Configuration, Security, and Troubleshooting
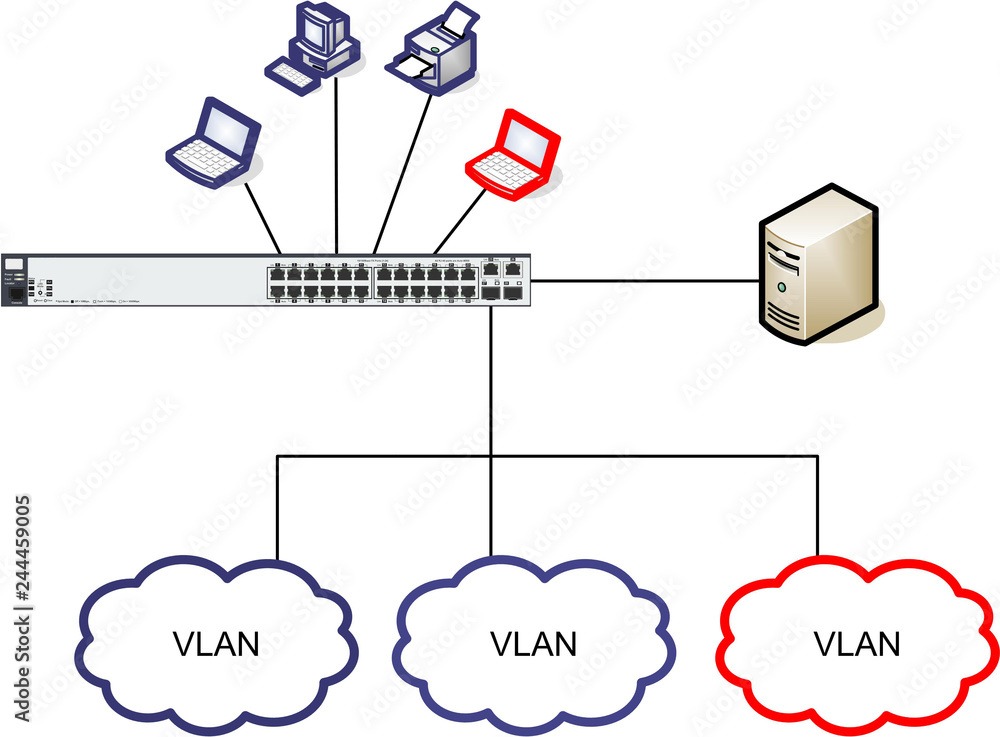
What is a VLAN?
A VLAN (Virtual Local Area Network) is a logical grouping of network devices that allows devices to communicate as if they were on the same physical network, regardless of their physical location. VLANs are used to segment a network into smaller, manageable pieces, which can improve performance, enhance security, and simplify network management.
-
- Logical Segmentation: VLANs enable the creation of distinct broadcast domains within a single physical network infrastructure.
-
- Isolation: Devices in different VLANs cannot communicate with each other without a router or Layer 3 switch to handle inter-VLAN routing.
-
- Flexibility: Devices can be moved to different VLANs without needing physical changes to the network cabling.
Benefits of Using VLANs
1. Improved Network Performance:
-
- Reduced Broadcast Traffic: VLANs reduce the size of broadcast domains, minimizing broadcast traffic and reducing network congestion.
- Optimized Bandwidth Utilization: Traffic is confined to specific VLANs, ensuring that bandwidth is used more efficiently.
2. Enhanced Security:
- Segregation of Sensitive Data: Critical or sensitive data can be isolated on specific VLANs, limiting access to authorized users.
- Access Control: VLANs allow for the implementation of security policies and access controls at the network layer, providing better protection against unauthorized access.
3. Simplified Network Management:
- Easier Troubleshooting: Smaller, segmented networks are easier to manage and troubleshoot.
- Flexibility in Network Design: VLANs provide the flexibility to group devices based on function, department, or project, regardless of their physical location.
4. Cost Savings:
- Reduced Hardware Requirements: VLANs reduce the need for additional physical switches and routers, leading to cost savings on hardware and maintenance.
- Efficient Resource Utilization: Resources such as servers and storage can be shared across VLANs, optimizing their usage.
5. Improved Network Scalability:
- Logical Expansion: VLANs make it easier to add new devices and expand the network without significant changes to the physical infrastructure.
- Network Segmentation: Large networks can be segmented into smaller, manageable VLANs, improving overall network scalability.
Differences Between VLANs and Traditional LANs
1. Segmentation:
- Traditional LAN: All devices on a traditional LAN share the same broadcast domain, leading to potential congestion and security issues.
- VLAN: VLANs create multiple, isolated broadcast domains within a single physical network, reducing congestion and enhancing security.
2. Security:
- Traditional LAN: Devices on a traditional LAN can communicate freely, which can lead to security vulnerabilities.
- VLAN: VLANs isolate traffic, enhancing security by preventing unauthorized access and reducing the risk of broadcast storms.
3. Flexibility:
- Traditional LAN: Physical location dictates network segmentation, requiring physical changes to move devices.
- VLAN: VLANs provide logical segmentation, allowing devices to be moved or reconfigured without physical changes to the network infrastructure.
4. Management:
- Traditional LAN: Managing a large, flat network can be complex and time-consuming.
- VLAN: VLANs simplify network management by allowing administrators to segment the network logically, making it easier to apply policies and manage resources.
5. Performance:
- Traditional LAN: Broadcast traffic can negatively impact performance on large networks.
-
- VLAN: VLANs reduce broadcast traffic by creating smaller broadcast domains, improving overall network performance.
Types of VLANs
When configuring a VLAN system, it is essential to understand the different types of VLANs and their specific purposes. Here are the main types of VLANs you will encounter:
Default VLAN
- Description: The default VLAN is the initial VLAN configuration on a switch. It includes all the switch ports when the device is first powered on.
- Common Use: On most Cisco switches, VLAN 1 is the default VLAN.
- Special Characteristics:
- All switch ports are part of the default VLAN out of the box.
- Control traffic, such as CDP (Cisco Discovery Protocol) and spanning-tree protocol, often runs on the default VLAN.
- Best Practices: It’s generally recommended to avoid using VLAN 1 for user data traffic to enhance security and reduce potential issues with control traffic.
Data VLAN
- Description: Data VLANs, also known as user VLANs, are used to separate and segment user-generated data traffic.
- Common Use: Typically assigned to user devices like computers, printers, and other endpoints.
- Special Characteristics:
- Provides isolation between different user groups or departments within an organization.
- Can be configured based on different criteria such as department, function, or project.
- Best Practices: Use a specific range of VLAN IDs for data VLANs and implement access control measures to secure them.
Voice VLAN
- Description: Voice VLANs are dedicated VLANs used for VoIP (Voice over IP) traffic to ensure quality of service (QoS) and prioritize voice traffic over data traffic.
- Common Use: Assigned to IP phones and other VoIP devices.
- Special Characteristics:
- Provides a separate VLAN to manage voice traffic and ensures high-quality voice communications
- Requires proper QoS configurations to prioritize voice packets.
- Best Practices: Configure the switch to recognize and handle voice traffic separately, ensuring minimal latency and jitter for voice communications.
Management VLAN
- Description: The management VLAN is used for network management traffic, including accessing and managing network devices like switches, routers, and firewalls.
- Common Use: Typically assigned to network administrators’ workstations and network management systems.
- Special Characteristics:
- Provides a secure and dedicated VLAN for managing network infrastructure.
- Enhances security by isolating management traffic from user and data traffic.
- Best Practices: Ensure the management VLAN is highly secure, using strong authentication, access control, and encryption where possible.
Native VLAN
- Description: The native VLAN is used for untagged traffic received on a trunk port. It is the VLAN that any untagged frames are assigned to when they arrive at a switch.
- Common Use: Often set to VLAN 1 by default, but best practice is to change it to a different VLAN ID to enhance security.
- Special Characteristics:
- Only one native VLAN is configured per trunk link.
- Provides backward compatibility with devices that do not support VLAN tagging.
- Best Practices: Avoid using VLAN 1 as the native VLAN and choose a VLAN ID that is not used for other purposes to minimize security risks.
Detailed Example: Configuring Different Types of VLANs on a Cisco Switch
Step-by-Step Guide:
-
- Access the Switch:
-
- Connect to the switch using console, SSH, or Telnet.
-
- Enter privileged EXEC mode:
bash enable
- Enter privileged EXEC mode:
-
- Enter global configuration mode:
bash configure terminal
- Enter global configuration mode:
-
- Create Data VLANs (e.g., VLAN 10 for Sales, VLAN 20 for Marketing):
vlan 10
name Sales
exit
vlan 20
name Marketing
exit-
- Create a Voice VLAN (e.g., VLAN 30):
vlan 30
name Voice
exit-
- Create a Management VLAN (e.g., VLAN 40):
vlan 40
name Management
exit-
- Configure Ports for Data VLANs:
-
- Assign port FastEthernet 0/1 to VLAN 10 (Sales):
bash interface fastethernet0/1 switchport mode access switchport access vlan 10 exit
- Assign port FastEthernet 0/1 to VLAN 10 (Sales):
-
- Assign port FastEthernet 0/2 to VLAN 20 (Marketing):
bash interface fastethernet0/2 switchport mode access switchport access vlan 20 exit
- Assign port FastEthernet 0/2 to VLAN 20 (Marketing):
-
- Configure Port for Voice VLAN:
-
- Assign port FastEthernet 0/3 to VLAN 30 (Voice):
bash interface fastethernet0/3 switchport mode access switchport voice vlan 30 exit
- Assign port FastEthernet 0/3 to VLAN 30 (Voice):
-
- Configure a Trunk Port and Set Native VLAN (e.g., VLAN 99):
vlan 99
name Native
exit
interface fastethernet0/24
switchport mode trunk
switchport trunk native vlan 99
switchport trunk allowed vlan 10,20,30,40
exit
-
- Assign Management VLAN IP Address:
-
- Assign an IP address to the management VLAN interface:
bash interface vlan 40 ip address 192.168.40.1 255.255.255.0 exit
- Assign an IP address to the management VLAN interface:
-
- Save Configuration:
end
write memoryVLAN Tagging and Frame Format
VLAN tagging is a method used to identify and manage traffic from different VLANs on a network. This process follows the IEEE 802.1Q standard, which defines how VLAN tagging should be implemented and how VLAN information is added to Ethernet frames.
IEEE 802.1Q Standard
-
- Definition: IEEE 802.1Q is the networking standard that supports VLAN tagging in Ethernet frames, enabling multiple VLANs to share the same physical infrastructure.
-
- Purpose: The standard allows for the creation of multiple logical networks (VLANs) on a single physical network, facilitating better network segmentation, improved security, and enhanced traffic management.
-
- Key Features:
-
- Tagging: Adds a 4-byte tag to Ethernet frames to identify the VLAN.
-
- Trunking: Supports the concept of trunk ports that can carry traffic for multiple VLANs, distinguishing between them using VLAN tags.
VLAN Tagging Process
-
- Frame Generation:
-
- A device (e.g., a computer or an IP phone) generates an Ethernet frame for transmission.
-
- Tag Insertion:
-
- When the frame reaches a switch port configured as a trunk, a VLAN tag is inserted into the frame. This tag contains VLAN information that identifies the frame’s VLAN membership.
-
- Transmission:
-
- The tagged frame is transmitted across the network, through trunk links that carry traffic for multiple VLANs.
-
- Tag Removal:
-
- When the tagged frame reaches an access port on the destination switch, the VLAN tag is removed, and the frame is forwarded to the appropriate VLAN.
-
- Frame Reception:
-
- The device at the receiving end processes the frame as if it were on the same VLAN as the sender.
Understanding the VLAN Header and Frame Format
The VLAN tag is inserted into the Ethernet frame between the Source MAC address field and the EtherType/Length field. This insertion results in the frame format defined by the IEEE 802.1Q standard.
VLAN Tag Components
-
- Tag Protocol Identifier (TPID):
-
- Size: 2 bytes
-
- Value: 0x8100 (indicates that the frame is tagged with IEEE 802.1Q)
-
- Tag Control Information (TCI):
-
- Size: 2 bytes
-
- Subfields:
-
- Priority Code Point (PCP): 3 bits (indicates the priority level of the frame, used for Quality of Service)
-
- Drop Eligible Indicator (DEI): 1 bit (indicates if the frame can be dropped under congestion)
-
- VLAN Identifier (VID): 12 bits (identifies the VLAN to which the frame belongs, allowing for 4096 possible VLANs)
-
- Subfields:
IEEE 802.1Q Frame Format
Below is the structure of an Ethernet frame with a VLAN tag inserted:
| Field | Size (bytes) | Description |
|---|---|---|
| Destination MAC | 6 | MAC address of the destination |
| Source MAC | 6 | MAC address of the source |
| TPID | 2 | Tag Protocol Identifier (0x8100 for 802.1Q) |
| TCI | 2 | Tag Control Information (PCP, DEI, VID) |
| EtherType/Length | 2 | Indicates the type of payload |
| Payload | 46-1500 | Data carried by the frame |
| FCS | 4 | Frame Check Sequence for error detection |
Example of a VLAN Tagged Frame
Consider an Ethernet frame being sent from a computer in VLAN 10 with a priority of 5. The frame would be tagged as follows:
-
- Destination MAC: 00:11:22:33:44:55
-
- Source MAC: 66:77:88:99:AA:BB
-
- TPID: 0x8100
-
- TCI:
-
- PCP: 101 (binary for priority 5)
-
- DEI: 0 (frame is not drop-eligible)
-
- VID: 0000000001010 (binary for VLAN 10)
-
- EtherType: 0x0800 (indicating IPv4)
-
- Payload: Actual data
-
- FCS: Error checking value
VLAN Configuration
Configuring VLANs on network devices involves creating VLANs, naming them, assigning ports, and choosing between static and dynamic VLAN configurations. Here’s a detailed guide on how to perform VLAN configuration on different network devices, including Cisco and Juniper.
Configuring VLANs on Cisco Devices
Step 1: Access the Switch
-
- Connect to the switch using console, SSH, or Telnet.
-
- Enter privileged EXEC mode:
enable-
- Enter global configuration mode:
configure terminalStep 2: Create and Name VLANs
-
- Create VLAN 10 (Sales) and VLAN 20 (Marketing):
vlan 10
name Sales
exit
vlan 20
name Marketing
exitStep 3: Assign Ports to VLANs
-
- Assign port FastEthernet 0/1 to VLAN 10:
interface fastethernet0/1
switchport mode access
switchport access vlan 10
exit-
- Assign port FastEthernet 0/2 to VLAN 20:
interface fastethernet0/2
switchport mode access
switchport access vlan 20
exitStep 4: Save Configuration
-
- Save the configuration:
end
write memoryConfiguring VLANs on Juniper Devices
Step 1: Access the Switch
-
- Connect to the switch using console, SSH, or Telnet.
-
- Enter configuration mode:
configureStep 2: Create and Name VLANs
-
- Create VLAN 10 (Sales) and VLAN 20 (Marketing):
set vlans Sales vlan-id 10
set vlans Marketing vlan-id 20Step 3: Assign Ports to VLANs
-
- Assign port ge-0/0/1 to VLAN 10:
set interfaces ge-0/0/1 unit 0 family ethernet-switching port-mode access
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members Sales-
- Assign port ge-0/0/2 to VLAN 20:
set interfaces ge-0/0/2 unit 0 family ethernet-switching port-mode access
set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members MarketingStep 4: Commit Configuration
-
- Commit the configuration:
commitStatic VLAN Configuration
Static VLANs are manually assigned to switch ports. This configuration does not change unless an administrator manually modifies it. The steps to configure static VLANs are the same as those mentioned above for both Cisco and Juniper devices.
Dynamic VLAN Configuration using GVRP
GVRP (GARP VLAN Registration Protocol) allows dynamic VLAN registration and management. Here’s how you can configure dynamic VLANs using GVRP on Cisco devices.
Step 1: Enable GVRP on the Switch
-
- Enable GVRP globally:
configure terminal
gvrpStep 2: Configure GVRP on Trunk Ports
-
- Enable GVRP on trunk port FastEthernet 0/24:
interface fastethernet0/24
switchport mode trunk
gvrp enable
exitStep 3: Verify GVRP Configuration
-
- Verify GVRP status and VLAN registration:
show gvrpVerification Commands
After configuring VLANs, it’s essential to verify that the configuration is correct.
On Cisco Devices
-
- Verify VLANs:
show vlan brief-
- Verify trunk ports:
show interfaces trunk
-
- Verify VLAN assignment to ports:
show interfaces switchportOn Juniper Devices
-
- Verify VLANs:
show vlans-
- Verify interface configuration:
show configuration interfacesVLAN Trunking
What is VLAN Trunking?
VLAN trunking is a method used to extend VLANs across multiple switches, allowing VLAN traffic to pass between switches. Trunking enables VLANs to span multiple switches, maintaining VLAN segmentation throughout the network. This is achieved by tagging frames with VLAN identifiers as they traverse trunk links.
-
- Purpose: Trunking is used to carry traffic for multiple VLANs over a single physical link between network devices, such as switches or routers. This is essential in larger networks where VLANs are distributed across different switches.
Trunking Protocols
There are two primary protocols used for VLAN trunking:
-
- IEEE 802.1Q:
-
- Standard: The IEEE 802.1Q standard is the most widely used trunking protocol.
-
- Tagging: Adds a 4-byte tag to Ethernet frames to indicate the VLAN ID. The tag includes information such as the VLAN identifier (VID) and priority code point (PCP).
-
- Compatibility: IEEE 802.1Q is vendor-neutral and compatible with most modern networking equipment.
-
- Inter-Switch Link (ISL):
-
- Proprietary Protocol: ISL is a proprietary trunking protocol developed by Cisco.
-
- Encapsulation: Encapsulates the original Ethernet frame with an additional header, which includes the VLAN ID and other information.
-
- Usage: Although once popular in Cisco networks, ISL is now largely deprecated in favor of IEEE 802.1Q.
Configuring Trunk Ports on Switches
Configuring Trunk Ports on Cisco Switches
-
- Enter global configuration mode:
configure terminal-
- Select the interface to configure as a trunk port (e.g., FastEthernet 0/24):
interface fastethernet0/24-
- Set the interface to trunk mode:
switchport mode trunk-
- Specify the VLANs allowed on the trunk port:
switchport trunk allowed vlan 10,20-
- Exit interface configuration mode:
exit-
- Save the configuration:
end
write memoryConfiguring Trunk Ports on Juniper Switches
-
- Enter configuration mode:
configure-
- Select the interface to configure as a trunk port (e.g., ge-0/0/24):
set interfaces ge-0/0/24 unit 0 family ethernet-switching port-mode trunk-
- Specify the VLANs allowed on the trunk port:
set interfaces ge-0/0/24 unit 0 family ethernet-switching vlan members [10 20]-
- Commit the configuration:
commitAllowed VLANs on Trunk Ports
When configuring trunk ports, it’s crucial to specify which VLANs are allowed to pass through the trunk. By default, all VLANs are allowed, but you can restrict this to specific VLANs for security and performance reasons.
Example for Cisco Switches
-
- Enter global configuration mode:
configure terminal-
- Select the trunk port interface:
interface fastethernet0/24-
- Specify allowed VLANs (e.g., VLANs 10 and 20):
switchport trunk allowed vlan 10,20-
- Exit interface configuration mode and save the configuration:
exit
end
write memoryExample for Juniper Switches
-
- Enter configuration mode:
configure-
- Select the trunk port interface:
set interfaces ge-0/0/24 unit 0 family ethernet-switching vlan members [10 20]-
- Commit the configuration:
commitVLAN Management
Effective VLAN management involves several practices and tools to ensure network performance, security, and scalability. This includes using VLAN Management Policy Server (VMPS), VLAN membership policies, and VLAN pruning.
VLAN Management Policy Server (VMPS)
A VLAN Management Policy Server (VMPS) is a Cisco feature that dynamically assigns switch ports to VLANs based on the MAC addresses of the connected devices. VMPS simplifies VLAN management by automating the process of VLAN assignment, thus reducing administrative overhead and minimizing configuration errors.
Key Components of VMPS:
-
- VMPS Server: The central server that holds the database of MAC address-to-VLAN mappings.
-
- VMPS Clients: Switches that query the VMPS server to determine the appropriate VLAN for a given MAC address.
VMPS Configuration Steps:
-
- Configure the VMPS Server:
-
- Define the VLAN-to-MAC address mappings on the VMPS server.
-
- Example configuration on a Cisco switch acting as the VMPS server:
bash vmps server <VMPS_SERVER_IP_ADDRESS> vmps domain <DOMAIN_NAME>
- Example configuration on a Cisco switch acting as the VMPS server:
-
- Configure VMPS Clients:
-
- Set the switch to operate as a VMPS client.
-
- Example configuration on a Cisco switch acting as a VMPS client:
bash vmps client vmps server <VMPS_SERVER_IP_ADDRESS>
- Example configuration on a Cisco switch acting as a VMPS client:
-
- Create and populate the VMPS database:
-
- Define the mappings of MAC addresses to VLANs.
-
- Example database entry:
vmps-db mac-address 00:11:22:33:44:55 vlan 10 mac-address 66:77:88:99:AA:BB vlan 20
- Example database entry:
VLAN Membership Policy
A VLAN membership policy defines the criteria for assigning devices to VLANs. This can be based on various factors, such as:
-
- Port-based: Assigning VLANs based on the physical port a device is connected to.
-
- MAC address-based: Using the MAC address of a device to determine its VLAN assignment (as in VMPS).
-
- Protocol-based: Assigning VLANs based on the protocols being used by the devices.
-
- User-based: Using authentication mechanisms like 802.1X to assign VLANs based on user credentials.
Implementing VLAN Membership Policy:
-
- Port-based VLAN Assignment:
-
- Example configuration on a Cisco switch:
bash interface fastethernet0/1 switchport mode access switchport access vlan 10
- Example configuration on a Cisco switch:
-
- MAC Address-based VLAN Assignment:
-
- Example configuration using VMPS (as described above).
-
- Protocol-based VLAN Assignment:
-
- Example configuration to assign VLANs based on IP protocols:
bash interface fastethernet0/1 switchport mode access switchport voice vlan 20
- Example configuration to assign VLANs based on IP protocols:
-
- User-based VLAN Assignment:
-
- Example configuration using 802.1X authentication:
bash interface fastethernet0/1 authentication port-control auto dot1x pae authenticator
- Example configuration using 802.1X authentication:
VLAN Pruning to Optimize Traffic
VLAN pruning is the process of limiting the distribution of VLAN traffic to only the parts of the network that require it. This helps reduce unnecessary broadcast traffic, thus optimizing network performance and conserving bandwidth.
How VLAN Pruning Works:
-
- Manual Pruning: Administratively configure which VLANs are allowed on each trunk link.
-
- Automatic Pruning: Utilize features like Cisco’s VTP Pruning to dynamically manage VLAN traffic on trunks.
Manual VLAN Pruning:
-
- Enter global configuration mode:
configure terminal
-
- Select the trunk port interface:
interface fastethernet0/24
-
- Specify the VLANs allowed on the trunk port:
switchport trunk allowed vlan 10,20
-
- Exit interface configuration mode and save the configuration:
exit
end
write memoryAutomatic VLAN Pruning with VTP Pruning:
-
- Enable VTP Pruning:
configure terminal
vtp pruning
end
-
- Verify VTP Pruning status:
show vtp statusVLAN Security
VLANs (Virtual Local Area Networks) are integral to network segmentation and organization, but they also introduce security considerations that need careful management to prevent vulnerabilities and attacks. Here’s a comprehensive look at VLAN security issues, best practices, Private VLANs (PVLANs), and the use of Access Control Lists (ACLs) on VLANs.
Common VLAN Security Issues
-
- VLAN Hopping:
-
- Description: VLAN hopping occurs when an attacker gains unauthorized access to traffic from a VLAN other than their own. This can happen due to misconfigurations or weaknesses in the network infrastructure.
-
- Types:
-
- Switch Spoofing: Exploiting Dynamic Trunking Protocol (DTP) or VLAN Trunking Protocol (VTP) to gain access to all VLANs on a trunk.
-
- Double Tagging: Sending packets with two VLAN tags to bypass switch security.
-
- Types:
-
- Mitigation: Disable unused ports, disable DTP/VTP where unnecessary, and implement VLAN access controls.
-
- Double Tagging:
-
- Description: An attacker sends packets with multiple VLAN tags to confuse switches and gain access to multiple VLANs.
-
- Mitigation: Configure switches to drop packets with more than one VLAN tag (
vlan dot1q tag native) and use VLAN ACLs to filter out unauthorized traffic.
- Mitigation: Configure switches to drop packets with more than one VLAN tag (
Best Practices for Securing VLANs
-
- Disable Unused Ports:
-
- Description: Ensure that unused switch ports are administratively shut down to prevent unauthorized access or VLAN hopping.
-
- Implementation: Use commands like
shutdownorswitchport mode accesswithshutdownto disable ports.
- Implementation: Use commands like
-
- Use VLAN ACLs:
-
- Description: Implement Access Control Lists (ACLs) to filter traffic entering or leaving VLANs, based on IP addresses, protocols, or other criteria.
-
- Implementation: Configure VLAN ACLs on layer 3 interfaces or SVIs (Switched Virtual Interfaces).
-
- Port Security:
-
- Description: Limit the number of MAC addresses or specify allowed MAC addresses per switch port to prevent unauthorized devices from connecting.
-
- Implementation: Configure port security using commands like
switchport port-security.
- Implementation: Configure port security using commands like
-
- VLAN Trunking Security:
-
- Description: Secure trunk links to prevent VLAN hopping and unauthorized access.
-
- Implementation: Use
switchport mode trunk, limit allowed VLANs withswitchport trunk allowed vlan, disable DTP/VTP where not needed, and enable features like BPDU guard and Root guard.
- Implementation: Use
Private VLANs (PVLANs)
-
- Description: Private VLANs (PVLANs) enhance VLAN security by partitioning a VLAN into sub-VLANs, each isolated from the others, while sharing a common gateway. PVLANs are categorized into:
-
- Primary VLAN: The main VLAN that is divided into secondary PVLANs.
-
- Secondary VLANs: These are isolated from each other but can communicate with devices in the primary VLAN.
-
- Community VLANs: Devices in the same community VLAN can communicate with each other and with devices in the primary VLAN.
-
- Implementation: Configure PVLANs on Cisco switches using commands like
switchport mode private-vlan.
- Implementation: Configure PVLANs on Cisco switches using commands like
Access Control Lists (ACLs) on VLANs
-
- Description: VLAN ACLs filter traffic based on Layer 3 and Layer 4 information, such as IP addresses, protocols, or port numbers. They can be applied to VLANs to control traffic entering or leaving specific VLANs.
-
- Implementation: Configure VLAN ACLs using:
-
- Standard ACLs: Filter traffic based on source IP addresses.
-
- Extended ACLs: Filter traffic based on source and destination IP addresses, ports, and protocols.
-
- VLAN ACLs are applied on layer 3 interfaces or SVIs using commands like
ip access-group.
- VLAN ACLs are applied on layer 3 interfaces or SVIs using commands like
Designing VLANs involves careful planning to ensure scalability, performance, and ease of management. Here are best practices and guidelines for designing VLANs, considering scalability, performance, VLAN naming conventions, and documentation/change management:
Guidelines for Designing VLANs
1. Scalability Considerations
-
- Purpose-Driven VLANs: Design VLANs based on functional or departmental purposes rather than physical locations. This ensures scalability as the network grows.
-
- Hierarchical Structure: Implement a hierarchical VLAN design (core, distribution, access layers) to support scalability and ease of management.
-
- Avoid Overlapping: Ensure VLAN IDs do not overlap across different parts of the network to prevent conflicts and simplify troubleshooting.
2. Performance Considerations
-
- Bandwidth Requirements: Group devices with similar bandwidth requirements into the same VLAN to optimize network performance.
-
- Traffic Segmentation: Use VLANs to segment traffic logically, reducing broadcast domains and improving overall network efficiency.
-
- QoS Implementation: Consider implementing Quality of Service (QoS) policies within VLANs to prioritize critical traffic and enhance performance for applications.
3. VLAN Naming Conventions
-
- Descriptive Names: Use clear and descriptive names for VLANs that reflect their purpose or function (e.g., Sales, Marketing, Servers).
-
- Consistency: Maintain consistency in VLAN naming conventions across the network to facilitate easier management and troubleshooting.
-
- Abbreviations: Use abbreviations when necessary but ensure they are easily understood by all network administrators.
4. Documentation and Change Management
-
- Network Diagrams: Maintain up-to-date network diagrams that document VLAN configurations, including VLAN IDs, names, and associated devices.
-
- Configuration Templates: Use standardized configuration templates for creating VLANs across devices to ensure consistency and reduce errors.
-
- Change Control Procedures: Implement change control procedures to document VLAN modifications, approvals, and rollback plans to minimize network disruptions.
Example Implementation
Example VLAN Design
VLAN ID VLAN Name Purpose/Function
--------------------------------------------------------------
10 Sales Sales department computers
20 Marketing Marketing department computers
30 Servers Server farm and critical infrastructure
40 Wireless Wireless access points and clients
50 Management Network management devices (switches, routers)Example Documentation
-
- Network Diagram:

- Network Diagram:
-
- Configuration Template (Cisco):
vlan 10
name Sales
vlan 20
name Marketing
vlan 30
name Servers
vlan 40
name Wireless
vlan 50
name ManagementChange Management Example
-
- Change Request: Document any VLAN modifications, including VLAN ID changes or new VLAN creation.
-
- Approval Process: Obtain necessary approvals before implementing VLAN changes to minimize risks.
-
- Rollback Plan: Maintain a rollback plan in case of issues or unintended consequences from VLAN changes.
Designing VLANs involves careful planning to ensure scalability, performance, and ease of management. Here are best practices and guidelines for designing VLANs, considering scalability, performance, VLAN naming conventions, and documentation/change management:
Guidelines for Designing VLANs
1. Scalability Considerations
-
- Purpose-Driven VLANs: Design VLANs based on functional or departmental purposes rather than physical locations. This ensures scalability as the network grows.
-
- Hierarchical Structure: Implement a hierarchical VLAN design (core, distribution, access layers) to support scalability and ease of management.
-
- Avoid Overlapping: Ensure VLAN IDs do not overlap across different parts of the network to prevent conflicts and simplify troubleshooting.
2. Performance Considerations
-
- Bandwidth Requirements: Group devices with similar bandwidth requirements into the same VLAN to optimize network performance.
-
- Traffic Segmentation: Use VLANs to segment traffic logically, reducing broadcast domains and improving overall network efficiency.
-
- QoS Implementation: Consider implementing Quality of Service (QoS) policies within VLANs to prioritize critical traffic and enhance performance for applications.
3. VLAN Naming Conventions
-
- Descriptive Names: Use clear and descriptive names for VLANs that reflect their purpose or function (e.g., Sales, Marketing, Servers).
-
- Consistency: Maintain consistency in VLAN naming conventions across the network to facilitate easier management and troubleshooting.
-
- Abbreviations: Use abbreviations when necessary but ensure they are easily understood by all network administrators.
4. Documentation and Change Management
-
- Network Diagrams: Maintain up-to-date network diagrams that document VLAN configurations, including VLAN IDs, names, and associated devices.
-
- Configuration Templates: Use standardized configuration templates for creating VLANs across devices to ensure consistency and reduce errors.
-
- Change Control Procedures: Implement change control procedures to document VLAN modifications, approvals, and rollback plans to minimize network disruptions.
Example Implementation
Example VLAN Design
VLAN ID VLAN Name Purpose/Function
--------------------------------------------------------------
10 Sales Sales department computers
20 Marketing Marketing department computers
30 Servers Server farm and critical infrastructure
40 Wireless Wireless access points and clients
50 Management Network management devices (switches, routers)Example Documentation
-
- Network Diagram:

- Network Diagram:
-
- Configuration Template (Cisco):
vlan 10
name Sales
vlan 20
name Marketing
vlan 30
name Servers
vlan 40
name Wireless
vlan 50
name ManagementChange Management Example
-
- Change Request: Document any VLAN modifications, including VLAN ID changes or new VLAN creation.
-
- Approval Process: Obtain necessary approvals before implementing VLAN changes to minimize risks.
-
- Rollback Plan: Maintain a rollback plan in case of issues or unintended consequences from VLAN changes.
Designing VLANs involves careful planning to ensure scalability, performance, and ease of management. Here are best practices and guidelines for designing VLANs, considering scalability, performance, VLAN naming conventions, and documentation/change management:
Guidelines for Designing VLANs
1. Scalability Considerations
-
- Purpose-Driven VLANs: Design VLANs based on functional or departmental purposes rather than physical locations. This ensures scalability as the network grows.
-
- Hierarchical Structure: Implement a hierarchical VLAN design (core, distribution, access layers) to support scalability and ease of management.
-
- Avoid Overlapping: Ensure VLAN IDs do not overlap across different parts of the network to prevent conflicts and simplify troubleshooting.
2. Performance Considerations
-
- Bandwidth Requirements: Group devices with similar bandwidth requirements into the same VLAN to optimize network performance.
-
- Traffic Segmentation: Use VLANs to segment traffic logically, reducing broadcast domains and improving overall network efficiency.
-
- QoS Implementation: Consider implementing Quality of Service (QoS) policies within VLANs to prioritize critical traffic and enhance performance for applications.
3. VLAN Naming Conventions
-
- Descriptive Names: Use clear and descriptive names for VLANs that reflect their purpose or function (e.g., Sales, Marketing, Servers).
-
- Consistency: Maintain consistency in VLAN naming conventions across the network to facilitate easier management and troubleshooting.
-
- Abbreviations: Use abbreviations when necessary but ensure they are easily understood by all network administrators.
4. Documentation and Change Management
-
- Network Diagrams: Maintain up-to-date network diagrams that document VLAN configurations, including VLAN IDs, names, and associated devices.
-
- Configuration Templates: Use standardized configuration templates for creating VLANs across devices to ensure consistency and reduce errors.
-
- Change Control Procedures: Implement change control procedures to document VLAN modifications, approvals, and rollback plans to minimize network disruptions.
Example Implementation
Example VLAN Design
VLAN ID VLAN Name Purpose/Function
--------------------------------------------------------------
10 Sales Sales department computers
20 Marketing Marketing department computers
30 Servers Server farm and critical infrastructure
40 Wireless Wireless access points and clients
50 Management Network management devices (switches, routers)Example Documentation
-
- Network Diagram:

- Network Diagram:
-
- Configuration Template (Cisco):
vlan 10
name Sales
vlan 20
name Marketing
vlan 30
name Servers
vlan 40
name Wireless
vlan 50
name ManagementChange Management Example
-
- Change Request: Document any VLAN modifications, including VLAN ID changes or new VLAN creation.
-
- Approval Process: Obtain necessary approvals before implementing VLAN changes to minimize risks.
-
- Rollback Plan: Maintain a rollback plan in case of issues or unintended consequences from VLAN changes.
Troubleshooting VLANs
Troubleshooting VLANs involves identifying and resolving common issues related to VLAN configuration, connectivity, and traffic management. Here are insights into common VLAN issues, tools, commands, and real-world examples for troubleshooting VLAN problems:
Common VLAN Issues
-
- VLAN Configuration Errors:
-
- Incorrect VLAN IDs or names.
-
- VLANs not properly configured on switches or routers.
-
- VLAN mismatch between switches.
-
- VLAN Connectivity Issues:
-
- Devices in different VLANs unable to communicate.
-
- Inter-VLAN routing not configured or malfunctioning.
-
- VLAN trunking misconfigurations.
-
- Performance Problems:
-
- Broadcast storms affecting VLAN performance.
-
- Misconfigured QoS affecting VLAN traffic prioritization.
-
- VLAN traffic congestion due to inadequate bandwidth allocation.
Tools and Commands for Troubleshooting VLAN Problems
-
- Show Commands:
-
- show vlan brief: Displays a brief summary of VLANs configured on the switch.
-
- show interfaces trunk: Shows the status and configuration of trunk interfaces, including allowed VLANs.
-
- show interfaces switchport: Provides detailed information about switchport configurations, including VLAN assignments.
-
- Packet Sniffers:
-
- Tools like Wireshark can capture and analyze VLAN-tagged traffic to diagnose VLAN connectivity issues and packet drops.
-
- Ping and Traceroute:
-
- Use these tools to test connectivity between devices in different VLANs and troubleshoot routing or firewall issues.
-
- Debug Commands:
-
- debug vlan: Provides real-time debugging information about VLAN-related events and issues on the switch.
-
- debug spanning-tree: Helps troubleshoot VLAN connectivity problems related to Spanning Tree Protocol (STP) issues.
Analyzing VLAN Configuration and Traffic
-
- Review VLAN Configuration:
-
- Check VLAN IDs, names, and interface assignments across switches to ensure consistency and correctness.
-
- Verify trunk port configurations to ensure correct VLAN tagging and allowed VLANs.
-
- Traffic Analysis:
-
- Use network monitoring tools to analyze VLAN traffic patterns, identify bottlenecks, and detect abnormal traffic behaviors.
-
- Monitor VLAN interfaces or SVIs (Switched Virtual Interfaces) for traffic utilization and errors.
Case Studies and Real-World Examples
-
- Case Study: VLAN Configuration Error
-
- Issue: VLAN 10 was misconfigured on a switch, causing connectivity issues for devices in that VLAN.
-
- Solution: Corrected VLAN configuration on the switch and verified connectivity using ping and traceroute tools.
-
- Real-World Example: VLAN Trunking Issue
-
- Issue: Trunk port between two switches did not allow VLAN 20 traffic, affecting inter-VLAN communication.
-
- Solution: Updated trunk port configuration to include VLAN 20 using
switchport trunk allowed vlancommand and verified connectivity.
- Solution: Updated trunk port configuration to include VLAN 20 using
Conclusion
VLANs (Virtual Local Area Networks) are essential for network segmentation, security, and efficient traffic management in modern networking environments. Designing, configuring, and managing VLANs requires careful consideration of several factors, including scalability, performance, security, and troubleshooting practices.
By following best practices such as using hierarchical VLAN designs, implementing VLAN naming conventions, and documenting configurations with change management procedures, network administrators can ensure robust VLAN deployments. These practices not only enhance network performance and scalability but also simplify troubleshooting and maintenance tasks.
Furthermore, understanding VLAN security issues like VLAN hopping and implementing measures such as access control lists (ACLs) and Private VLANs (PVLANs) can significantly enhance VLAN security and protect against unauthorized access.
When troubleshooting VLAN issues, utilizing tools like show commands, packet sniffers, and debug commands allows for effective diagnosis of configuration errors, connectivity issues, and performance problems. Real-world examples and case studies demonstrate the application of these tools and practices in resolving VLAN-related challenges and maintaining network reliability.
In conclusion, VLANs are powerful tools for network administrators to optimize network efficiency and security. By adopting comprehensive VLAN management strategies, organizations can build resilient and scalable network infrastructures that meet the demands of modern connectivity.


